Error in Creating IAM User to Log in to the AWS Management Console – Explained and Solved
Creating IAM (Identity and Access Management) users in AWS is an essential step for managing access in cloud environments. However, users often encounter various errors during the setup process—especially when enabling login access to the AWS Management Console. In this article, we’ll walk through a correct, updated IAM user creation process and cover common issues and how to resolve them, helping you avoid frustration and get secure access set up in minutes.
AWS
7/28/20252 min read
Step-by-Step: How to Create an IAM User for Console Access
If you're setting up a new user to log in via the AWS Console, follow these steps carefully:
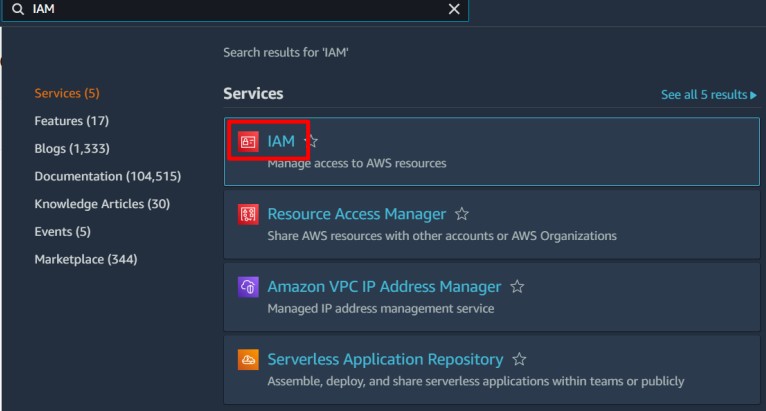
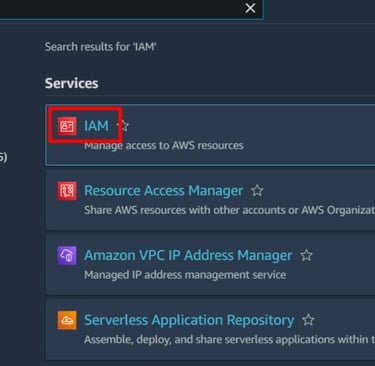
Step 1: Open IAM in AWS Console
Sign in to your AWS root or admin account.
Navigate to IAM under Security, Identity, and Compliance.
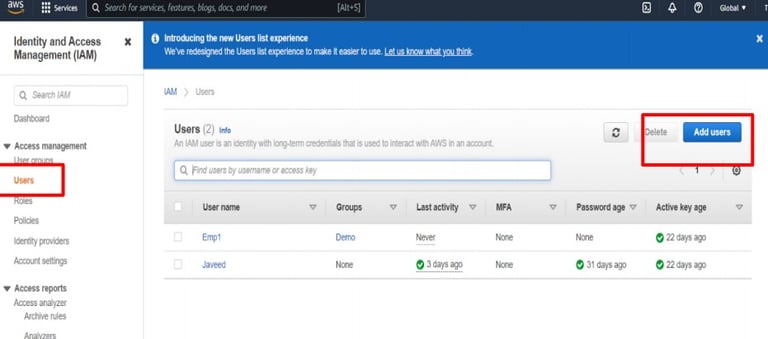
Step 2: Add a New User
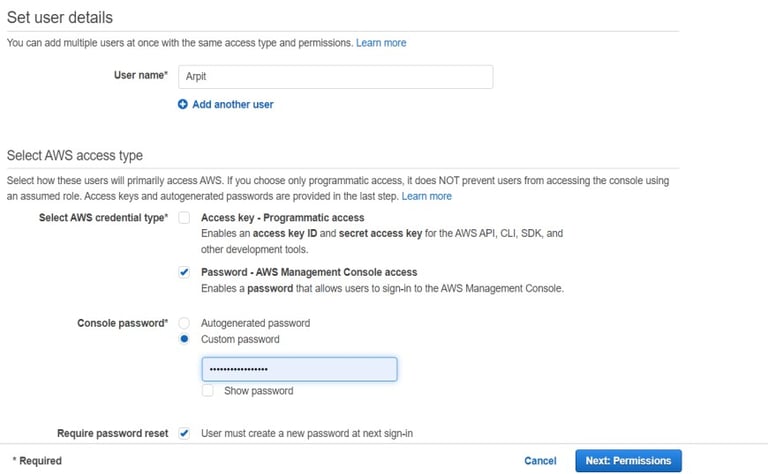
Click Users > Add user.
Enter a unique User name.
Under access type, enable "AWS Management Console access".
Choose whether to auto-generate a password or set a custom one.
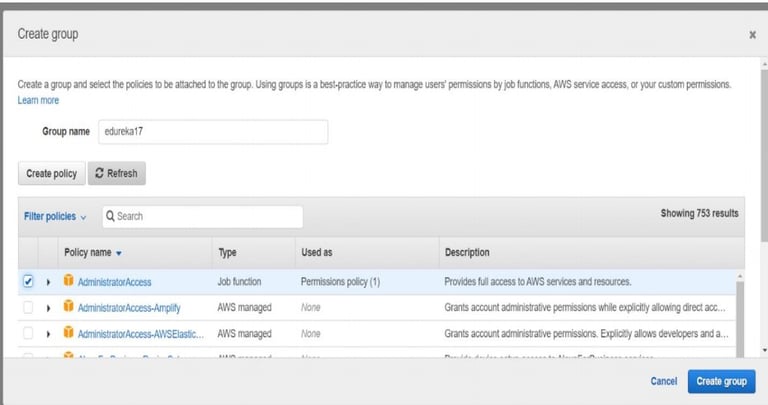
Step 3: Create a User Group
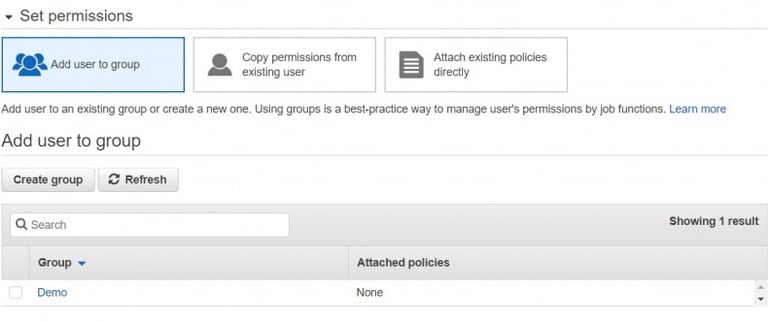
Click Create group.
Name your group (e.g., Developers, Admins).
Attach an appropriate IAM policy like:
AdministratorAccess
AmazonS3FullAccess
(Based on your need)
Step 4: Assign Group to User
After group creation, select the group and add the user to it.
Step 5: Finalize and Save Credentials
Click Next → Create user.
Note the console login URL and temporary password generated.
Step 6: First-Time Login
Paste the console login URL in a browser.
Enter the newly created IAM username and temporary password.
AWS will prompt you to set a new password.
Common Errors and Their Fixes
1. “User is not authorized to perform this action”
Cause: The user’s group or role lacks required permissions.
Fix: Attach appropriate IAM policies (like ReadOnlyAccess, AmazonEC2FullAccess, etc.) to the user or group.
2. “Your password must be reset before accessing AWS Management Console”
Cause: The user is logging in with the temporary password.
Fix: Complete the password reset during the first login.
3. “Invalid login URL”
Cause: Incorrect or partial IAM console link.
Fix: Use the format:
https://<account_alias>.signin.aws.amazon.com/console
Or retrieve the login URL from the IAM dashboard.
4. User does not appear in IAM list
Cause: User creation wasn’t completed.
Fix: Repeat the process and confirm the final step – “Create User”.
5. Access Denied after Login
Cause: No policies were attached to the user.
Fix: Ensure the user is part of a group with active IAM policies, or add policies directly to the user.
Conclusion
IAM setup may seem straightforward, but skipping even a small step can lead to frustrating login issues. Whether it’s missing permissions, an incorrect URL, or a forgotten password reset, this guide helps you troubleshoot and avoid common pitfalls.
Properly managing IAM users ensures secure access control and compliance with best practices on AWS.
#AWS, #IAM, #AWSErrorFix, #CloudSecurity, #AWSLoginIssue, #AWSConsole, #IAMUserSetup, #DevOps, #AmazonWebServices