Fixing AWS S3 Access Denied (403 Forbidden) – Step-by-Step Guide
If you’re working with Amazon S3 and get hit with the dreaded Access Denied (403) error, don’t panic. This is one of the most common S3 issues and usually boils down to permissions misconfiguration. This article will help you: Understand why this error happens, Troubleshoot common causes, Apply working solutions with code examples and AWS Console screenshots. Avoid it in future deployments
AWS
8/3/20252 min read
What Triggers S3 Access Denied (403)?
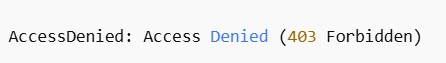
The error usually looks like this:
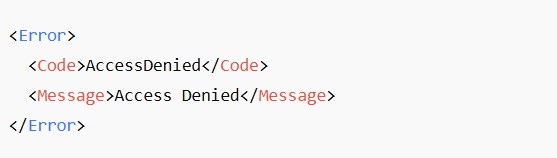
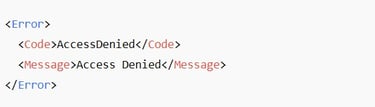
This happens when:
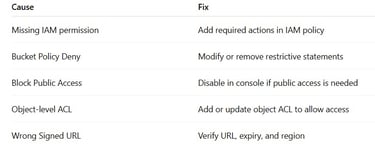
The IAM user/role lacks s3:* permissions
S3 Bucket Policies restrict access
Public access is blocked at the bucket/account level
You're accessing a bucket in the wrong AWS region
There's a mismatch in signed URL or object ACLs
1. Check IAM Permissions (The Usual Suspect)
Steps:
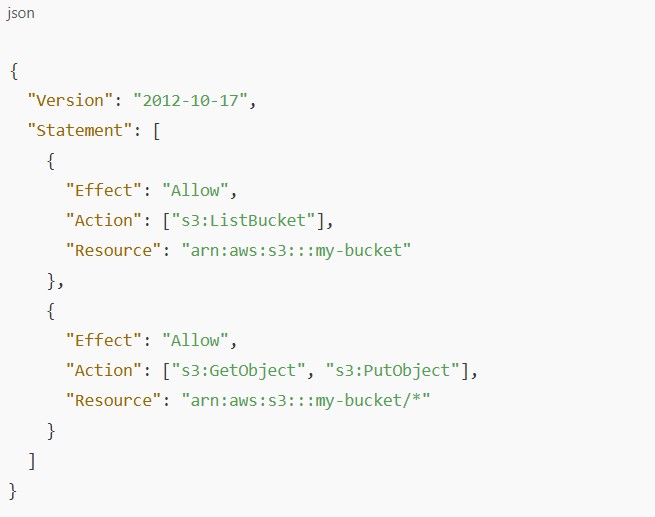
Go to IAM > Users > [your user] > Permissions
Ensure the attached policy includes actions like:
s3:GetObject
s3:PutObject
s3:ListBucket (for listing files)
2. Check the Bucket Policy (It Might Be Blocking You)
Go to S3 > [Your Bucket] > Permissions > Bucket Policy
Example of a Restrictive Policy
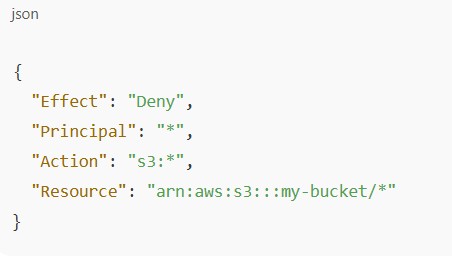
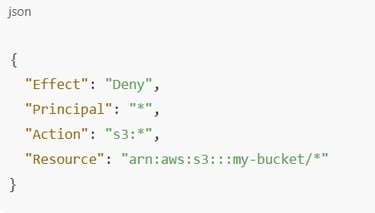
This denies everyone, including you.
Fix:
Remove or modify the Deny statement to allow specific users or roles access.
Sample Open Access Bucket Policy (with caution)
Example IAM Policy
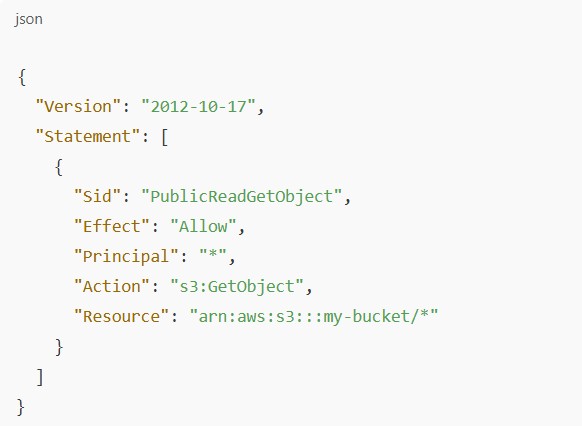
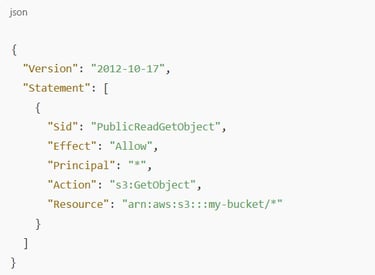
3. Disable “Block All Public Access” (If Hosting Public Content)
Even if you set a public policy, AWS will override it if this setting is ON.
Steps:
Go to S3 > Bucket > Permissions > Block public access
Click Edit
Uncheck the settings as needed
Save
🛑 Use this only if your use case requires public file access (like a static website)
4. Signed URLs: Common Pitfall
If you're using pre-signed URLs, a mismatch in the bucket name, region, or expiry can also result in 403.
Things to check:
Is the URL expired?
Is the bucket name correctly included?
Are you using the correct AWS region?
🧪 Test signed URL manually by visiting it in incognito mode.
5. Object ACLs – File-level Access Denied
Even if IAM and Bucket policies are okay, object-level ACLs might block you.
Steps:
Go to S3 > Bucket > Objects
Click on the object, go to Permissions
Make sure it has read permissions for intended users/public
Add Public ACL (if required)
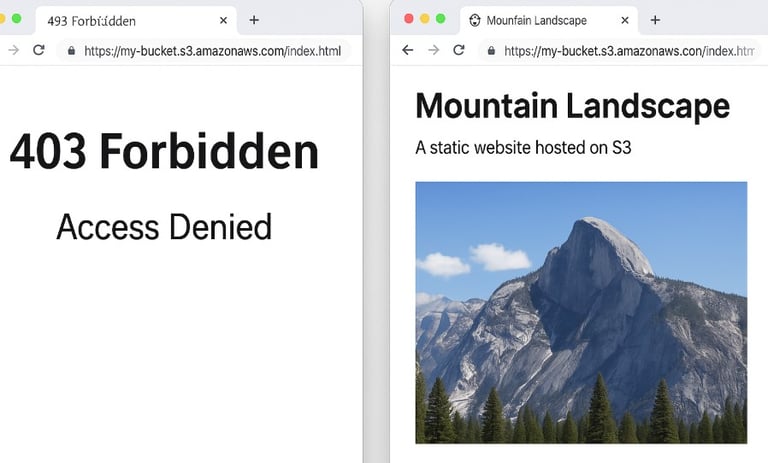
Real-World Example: Fixing S3 403 for a Static Website
Let's say you're hosting a static site on S3 and hit Access Denied when visiting https://my-bucket.s3.amazonaws.com/index.html.
Checklist:
Bucket is public
index.html exists
Bucket policy allows s3:GetObject
Block Public Access is disabled
The region matches the endpoint
Once these are fixed, the site loads correctly.
Summary: Troubleshooting S3 Access Denied (403)
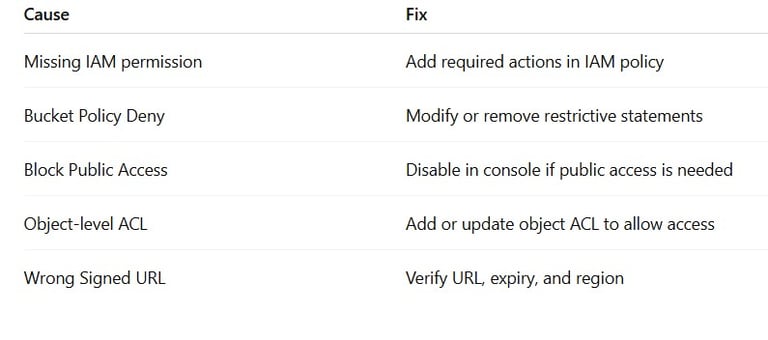
Final Tip: Use AWS Policy Simulator
Test your IAM + Bucket policies with the AWS Policy Simulator. It saves a lot of guesswork.